Russian troops and Kadyrovites set up arms smuggling through Crimea

The OSINT community InformNapalm has published the results of a leak of personal data belonging to Russian Armed Forces Major Yevgeny Dmitriev, obtained by the hacker group “256 Cyber Assault Division.” The leak exposed a network for the illegal sale of weapons from the front lines via occupied Crimea.
Major Dmitriev, commander of the assault platoon “Storm V” of the 291st Regiment, became the key source of evidence revealing systemic corruption within the Russian occupying forces. It was discovered that Russian officers, in collusion with the Kadyrovite battalion “Vostok-Akhmat,” established a steady channel for exporting rifles and ammunition, using “green corridors” controlled by the Russian National Guard at checkpoints along the R-280 highway.
Key findings of the operation:
- Crimea as an arms hub: The occupied peninsula has become a main transit base, from which smuggled weapons are shipped via tankers of Russia’s “shadow fleet” to Europe, Western Asia, and Africa.
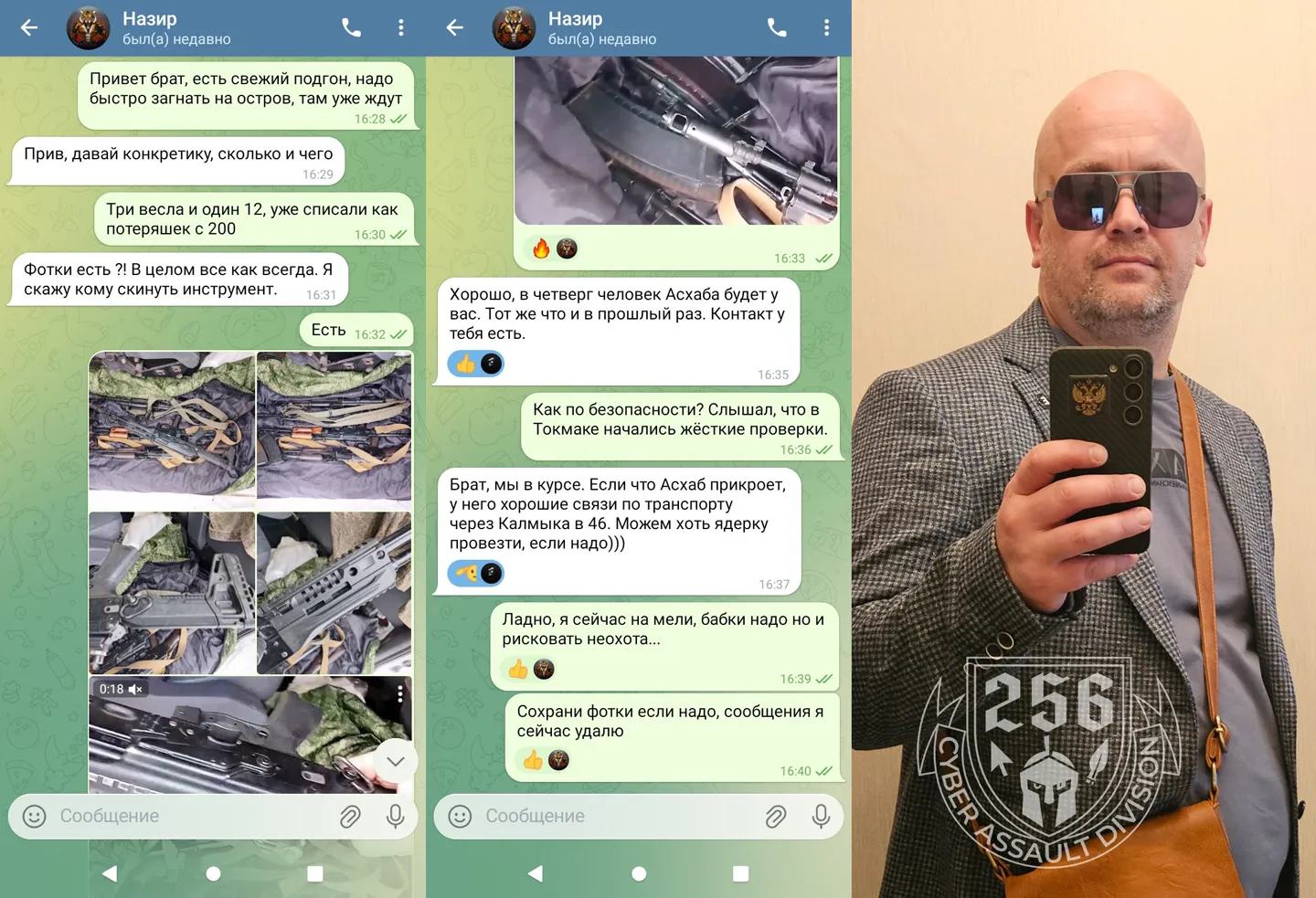
- “Write-off” schemes: Soldiers are sent into assaults without weapons or reported as losing them in battle, effectively creating surpluses of AK-12 and AK-74 rifles for sale. Each “written-off” rifle reportedly earns mid-level officers hundreds of dollars.
- Kadyrovite control: Logistics routes in Kherson and Zaporizhzhia are overseen by the 46th Separate Operational Brigade of the Russian National Guard, primarily made up of personnel from Chechnya. Their audacity reportedly includes statements such as: “We could even smuggle nuclear weapons if needed.”

- Elimination of competitors: The leak details the killing of the group leader Stanislav Orlov (“Espanyol”) in Sevastopol in December 2025, a result of a conflict over control of Crimea’s arms traffic.
Major Dmitriev’s case is illustrative of the current state of the Russian army: he signed a contract to avoid a prison term for drug trafficking. Despite diagnosed mental health issues, he was appointed to a command position. Ukrainian hackers gained access to his communications and carried out a sophisticated social engineering operation. Posing as Dmitriev, they contacted the administrators of the major Z-channel “Two Majors” and convinced them to transfer funds collected for the 291st Regiment to accounts controlled by Ukraine’s Special Operations Forces.
As a result, the money from Russian war supporters was converted into drones for Ukrainian defenders. Dmitriev has since been transferred to the Investigative Committee in occupied Donetsk, but all his previous activities—including videos of interrogations of his own soldiers and details of financial fraud—have been documented by Ukrainian intelligence.
This research confirms that corruption and internal conflicts within the Russian army remain one of the aggressor’s greatest vulnerabilities at the start of 2026.
Ukrainian hackers have previously hacked the website of the strategic aviation manufacturer Tupolev, as well as Russian television on Independence Day.


